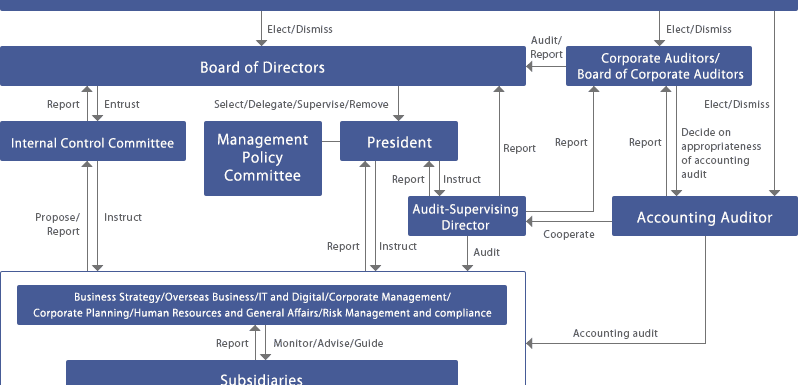
RAG
RAG is an advanced approach for building Large Language Model (LLM)-based systems capable of generating accurate, reliable, and contextually grounded responses by leveraging up-to-date information from an organization’s internal knowledge repositories. This method combines the generative power of AI language models with intelligent retrieval mechanisms that fetch the most relevant content from the organization’s knowledge base before formulating a response.